Office Add-in Security mode
Let's Start By Stating, iPlanner Pro, Office2SharePoint and MIPA are all safe and secure. We will be happy to provide you with a PEN test. Simply send us an email sales@iglobe.dk.
It is important to understand Office Add-ins
 In short, an Office Add-in extend Office applications and interact with content in Office. Office Add-ins, use familiar web technologies extend and interact with Word, Excel, PowerPoint, OneNote, Project, and Outlook. An Office Add-in can run in Office across multiple platforms, including Office for Windows, Office Online, Office for the Mac, and Office for IOS and Android.
In short, an Office Add-in extend Office applications and interact with content in Office. Office Add-ins, use familiar web technologies extend and interact with Word, Excel, PowerPoint, OneNote, Project, and Outlook. An Office Add-in can run in Office across multiple platforms, including Office for Windows, Office Online, Office for the Mac, and Office for IOS and Android.
Office Add-ins can do almost anything a webpage can do inside a browser. We can use an Office Add-in to:
-
Add new functionality to Office clients - Bring external data into Office, automate Office documents, expose third-party functionality in Office clients, and more. For example, use Microsoft Graph API to connect to data in Office 365 service like, Planner, SharePoint, Group, Exchange, etc.
-
Create new rich, interactive objects that can be embedded in Office documents - Embed maps, charts, and interactive visualizations that users can add to their own Excel spreadsheets and PowerPoint presentations.
How are Office Add-ins different than COM and VSTO add-ins?
COM or VSTO add-ins are earlier Office integration solutions that run only on Office for Windows. The add-in, that made your Outlook crash and required a lot of maintenance. You had to install these add-ins on each client and you had to update each client. A local installation with a potential security risks.
Unlike COM add-ins, Office Add-ins don't involve code that runs on the user's device or in the Office client.
For an Office Add-in, the host application, for example Outlook, reads the add-in manifest and hooks up the add-in’s custom ribbon buttons and menu commands in the UI. Then, when needed, it loads the add-in's JavaScript and HTML code which executes in the context of a browser in a sandbox.
Office Add-ins provide the following advantages over add-ins built using VBA, COM or VSTO:
-
Cross-platform support. Office Add-ins run in Office for Windows, Mac, iOS, and Office Online.
-
Single sign on (SSO). Office Add-ins integrate easily with users' Office 365 accounts.
-
Centralized deployment and distribution. Admins can deploy Office Add-ins centrally across an organization. This means, no local installation on any client and no updates on the local client
-
Easy access via the Office Store.
-
Based on standard web technology.
-
No conflict between installed Add-in that make the program crash
-
You are not bound to a specific version of foe example, Outlook or Excel because the COM add-in only support a specific version. With true Office Add-ins you simply follow the upgrades of Office and always be on the latest version and your Office Add-in will still work.
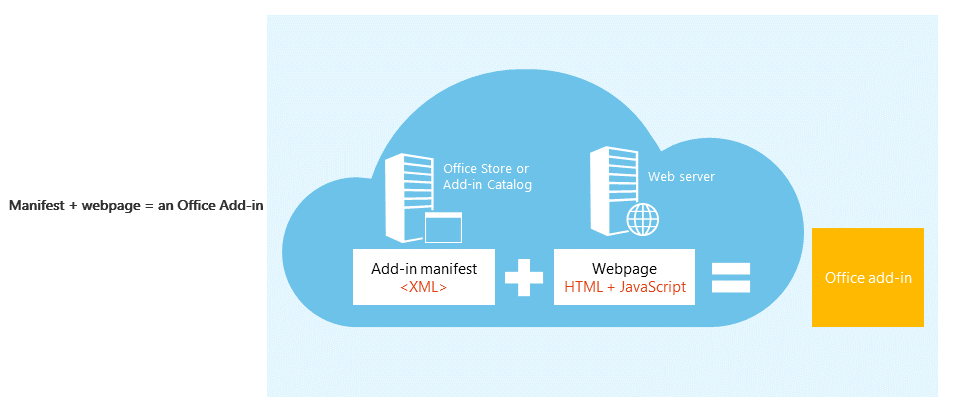
An Office Add-in includes two basic components: an XML manifest file, and the web application. The manifest defines various settings, including how the add-in integrates with Office clients. The web application needs to be hosted on a web server, or web hosting service, such as Microsoft Azure. This will often be on the Add-in Providers Azure.
Privacy and security for Office Add-ins.
Office add-ins combine an XML manifest file that contains some metadata about the add-in, but most importantly points to a web application which contains all the code and logic. Add-ins can range in their capabilities. For example, add-ins can:
-
Display data.
-
Read a user’s document to provide contextual services.
-
Read and write data to and from a user's document to provide value to that user.
For example, Office Add-in can bring data into Outlook, Office, automate Office documents, expose third-party functionality in Office clients, and more. For that purpose, Microsoft provide us with the Microsoft Graph API to connect to data in Office 365 service like, Planner, SharePoint, Group, Exchange, etc.
Microsoft Graph is a RESTful web API that enables you to access Microsoft Cloud service resources. After you register the Office Add-in and get authentication tokens for a user or service, you can make requests to the Microsoft Graph API.
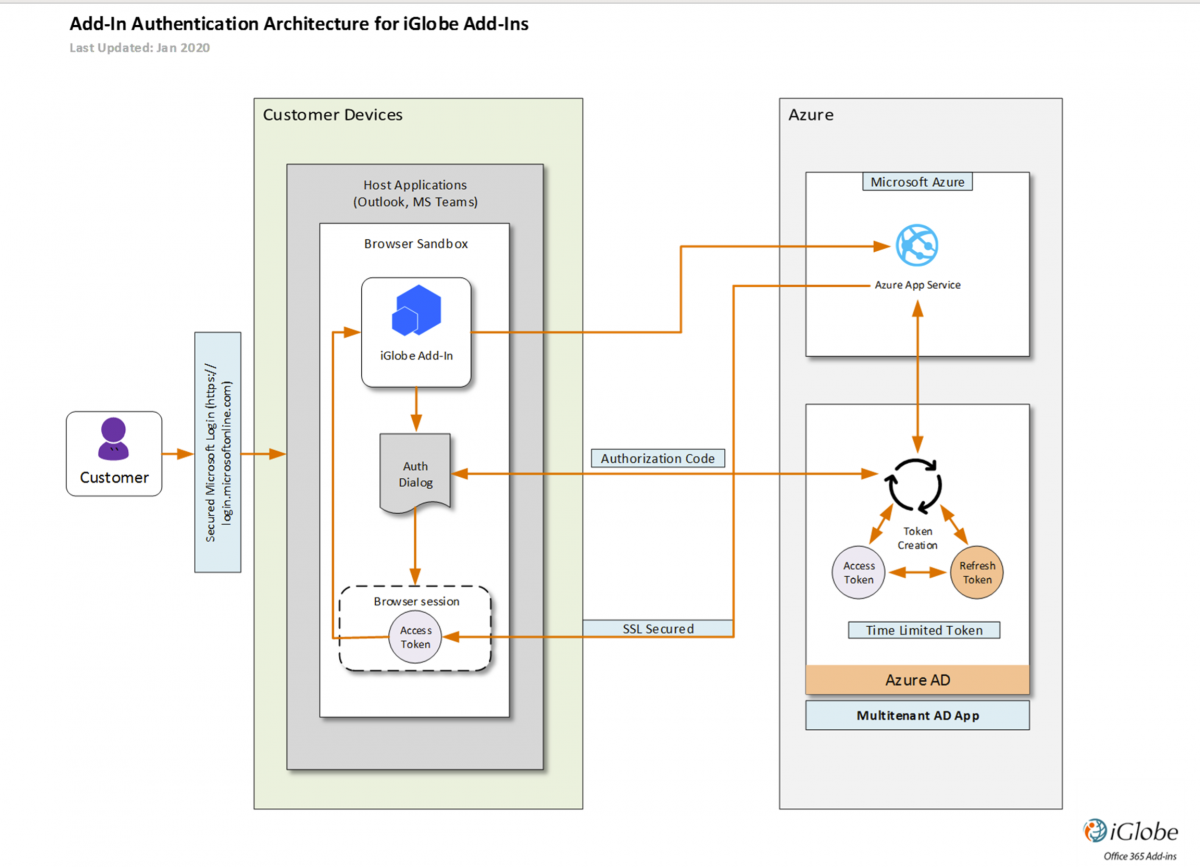
To call Microsoft Graph, the Add-in must acquire an access token from Azure Active Directory (Azure AD), Microsoft's cloud identity service. The access token contains information (or claims) about the Office Add-in and the permissions it has for the resources and APIs available through Microsoft Graph. To get an access token, the Add-in must be able to authenticate with Azure AD and be authorized by either a user or an administrator for access to the Microsoft Graph resources it needs.
What is an access token?
Access tokens issued by Azure AD are base 64 encoded JSON Web Tokens (JWT). They contain information (claims) that web APIs secured by Azure AD, like Microsoft Graph, use to validate the caller and to ensure that the caller has the proper permissions to perform the operation they're requesting. For a more detail description of
Token and Microsoft Graph security model
There are two types of permissions:
-
Delegated permissions are used by apps that run with a user present. The user's privileges are delegated to the Add-in which makes calls on behalf of the user to Microsoft Graph. Many of these permissions can be consented to by a user, and some others require administrator consent.
-
Application permissions are used by apps that run without a user. These often grant an app broad privileges within an organization and always require the consent of an administrator.
Office Add-ins from the Store are using Delegated permission
Microsoft Graph exposes a rich set of granular permissions over the resources it controls. These permissions grant Add-ins access to Microsoft Graph resources and Office 365 services like users, groups, user mail, SharePoint, Planner etc. Many of the Groups permission requires Administrator consent. More details about
Microsoft Graph permissions reference
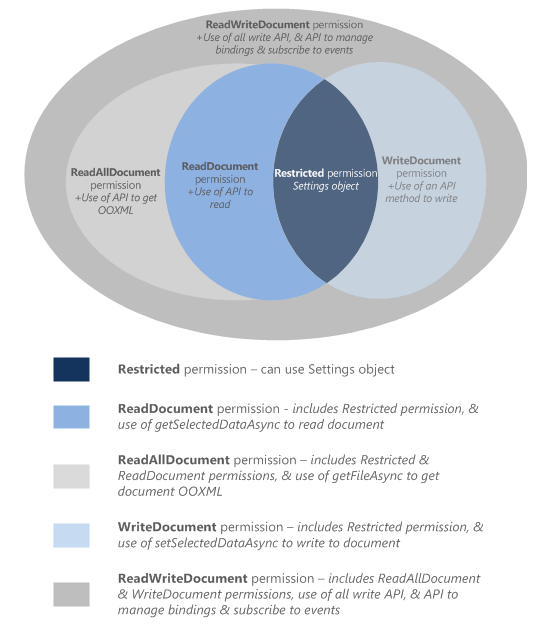
For allowing the Add-in to interact with the user's document, the add-in needs to declare what permission it needs in the manifest. A five-level JavaScript API access-permissions model provides the basis for privacy and security for users of task pane add-ins. The majority of the add-ins in the Office Store are level ReadWriteDocument with almost all add-ins supporting at least the ReadDocument level.
Administrator Consent
Effective permissions are the permissions the Add-in will have when making requests to Microsoft Graph.
For delegated permissions, the effective permissions of the Add-in will be the least privileged intersection of the delegated permissions the Add-in has been granted (via consent) and the privileges of the currently signed-in user. The Add-in can never have more privileges than the signed-in user.
Permission requires Administrator consent.
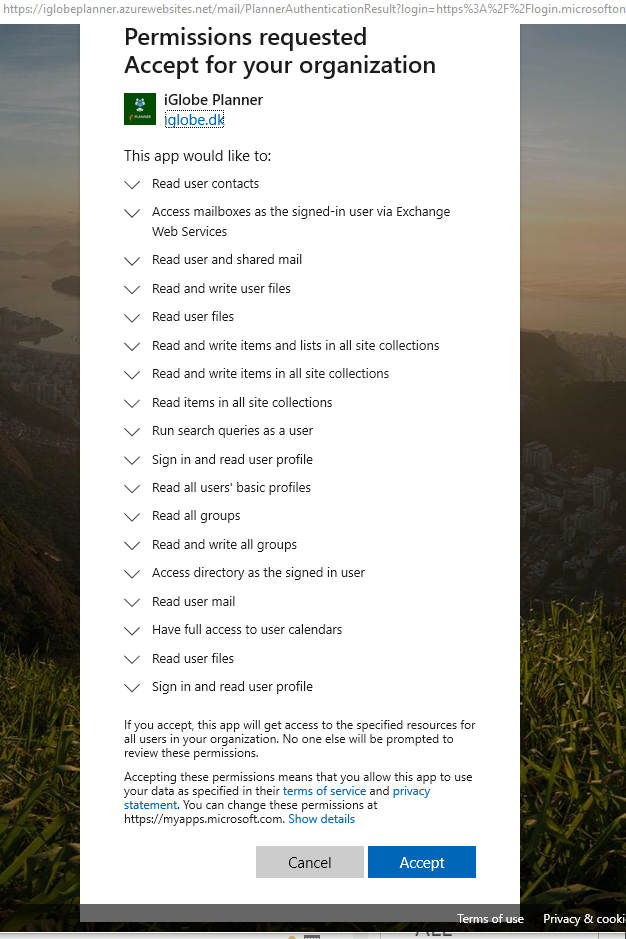
Administrator type users say “okay”. This means, users in the “Global admin” group can give an “ok” to the Add-in. And the “ok” is granted on behalf of all users in the Azure AD. End users therefore do not have to grant access, the access is granted on their behalf by the admin. Think of this as “let my organization use the Add-in with the required permission level necessary for the Add-in to provide the functionality you want”.
When an Office 365 Global administrator give consent to an Add-in, the administrator make sure only users from your Office 365 can get access to use the Add-in on your tenant and have permission to request data from the required services. The explained authentication and consent flow makes sure all other external will not get access. They haven’t been approved and don’t have a valid token nor consent or permission. The same goes for the Add-in provider, they don’t have access.
Let’s take an example of an Add-in provided by iGlobe – iPlanner Pro. This is an Outlook Add-in that extend Microsoft Planner into the users Outlook client and give the user the ability to manage and create Planner tasks directly from Outlook. iPlanner Pro is a web application which contains all the code and logic on iGlobe’s Azure. iPlanner Pro is following the above described authentication and consent flow 100%.
To able the functionality users will expect, iPlanner Pro requires permission to Planner, Exchange, Groups and SharePoint. To integrate to these services iPlanner Pro is using Microsoft Graph. iPlanner Pro is used by the user in Outlook and therefore requires delegated permissions. iPlanner Pro need a set of permission that will enable;
-
Display task information from the Online Planner
-
Create a task from Outlook in the Online Planner
-
Attach the selected mail to a task
-
Attach a document from the selected mail
-
Copy the subject and body text to the task
-
Save into your and the group calendar
-
Move a task from one Plan to another
-
Etc etc
It should be obvious that this will require a set of permission. Without having the required permissions, you will not get this functionality the Add-in is providing.
This means when a Global Administrator authenticate and give permission to iPlanner Pro you can think of this as “let my organization use the iPlanner Pro with the required permission level necessary for the iPlanner Pro to provide the functionality the users expect of the Add-in”.
Remember, it is the Add-in that interact with the required Office 365 services! IT ALL HAPPENS CLIENT SIDE! You don't give access to people outside your organization or to the Add-in provider. iGlobe do NOT save or have access to any App data, not do we save or have access to user App settings. iGlobe host the service the App is using. For iPlanner Pro, the host application, Outlook, reads the add-in manifest and hooks up the add-in’s custom ribbon buttons and menu commands in the UI. Then, when needed, it loads the add-in's JavaScript and HTML code which executes in the context of a browser in a sandbox. IT ALL HAPPENS ON YOUR TENANT!
Add-in updates
When updating a manifest, the typical changes are to an add-in's icon and text. Occasionally, add-in commands change. However, the permissions of the add-in do not change. The web application where all the code and logic for the add-in runs can change at any time, which is the nature of web applications.
If an add-in is updated in the Office Store it will update the dd-in next time the relevant Office applications start. The web application can change at any time and are “pushed” out by the Add-in provider. This means you do not have any updates on the local client.
Validated by Microsoft Office Store
Microsoft has an extremely strict policy to ensure that you will only get quality, secure and value-added Add-ins from the Store. For example, the validation team is testing the Add-in on all platform and browsers. If the permission level is set higher than required or give permission to more than necessary, the Add-in will be rejected. Beside that the validation team make sure of;
-
Apps and add-ins provide value to the Office Store customer
-
Apps and add-ins behave predictably
-
Apps and add-ins put the customer in control
-
Apps and add-ins are appropriate for a global audience
-
Apps and add-ins are easily identified and understood
iPlanner Pro - Microsoft 365 Certified App
Microsoft 365 App Certification offers assurance and confidence to enterprise organizations that data and privacy are adequately secured and protected when your Microsoft Word, Excel, PowerPoint, Outlook, Teams integration, or Graph API app is introduced to the Microsoft 365 platform. Certification confirms that an app solution is compatible with Microsoft technologies, compliant with cloud app security best practices, and supported by Microsoft, a trusted partner. App certification is achieved through the acceptance and approval of comprehensive documentation centering the app's security and compliance protocols, procedures, processes and a PEN test. Applications that pass validation will be designated Microsoft 365 App Certified.
iPlanner Pro score 10 out of 10 - Read more on Microsoft 365 App Security and Complianc site
Where is your data? And how about GDPR
This depends very much of the Add-in and the Add-in provider. However, most Office Add-in do not save any data locally on any device. As you recall Office Add-ins works across devices, all it requires is that the user is logged in to the Office 365 account. If data was saved locally you will not be able to use the add-in on different devices. This means no data is saved locally.
The Add-in provider can choose to save data on their web application or not. The described Add-in model do make it possible for the Add-in provider (ISV) to offer an Office Add-in that will not save any of your data. You will have to ask the Add-in provider about what data they save if any at all.
You will however see that most Add-in providers only save necessary information for the Add-in license management.
Can the Add-in Provider access your data? If no data is saved in the Add-in web application, this is a big NO! The authentication and consent model make sure of that. This means, that by following the Add-in security model and by not saving any of your data the Add-in itself is GDPR ready.
Deployment
As an Office 365 admin, you can deploy Office add-ins for the users in your organization. You can do this using the Centralized Deployment feature in the Office 365 admin center.
Centralized Deployment provides the following benefits:
-
An admin can assign an add-in directly to a user, to multiple users via a group, or to everyone in the tenant.
-
When the relevant Office application starts, the add-in automatically downloads for the user. If the add-in supports add-in commands, the add-in automatically appears in the Ribbon within the Office application.
-
Add-ins will no longer appear for users if the admin turns off or deletes the add-in, or if the user is removed from Azure Active Directory or from a group that the add-in is assigned to.
iPlanner Pro
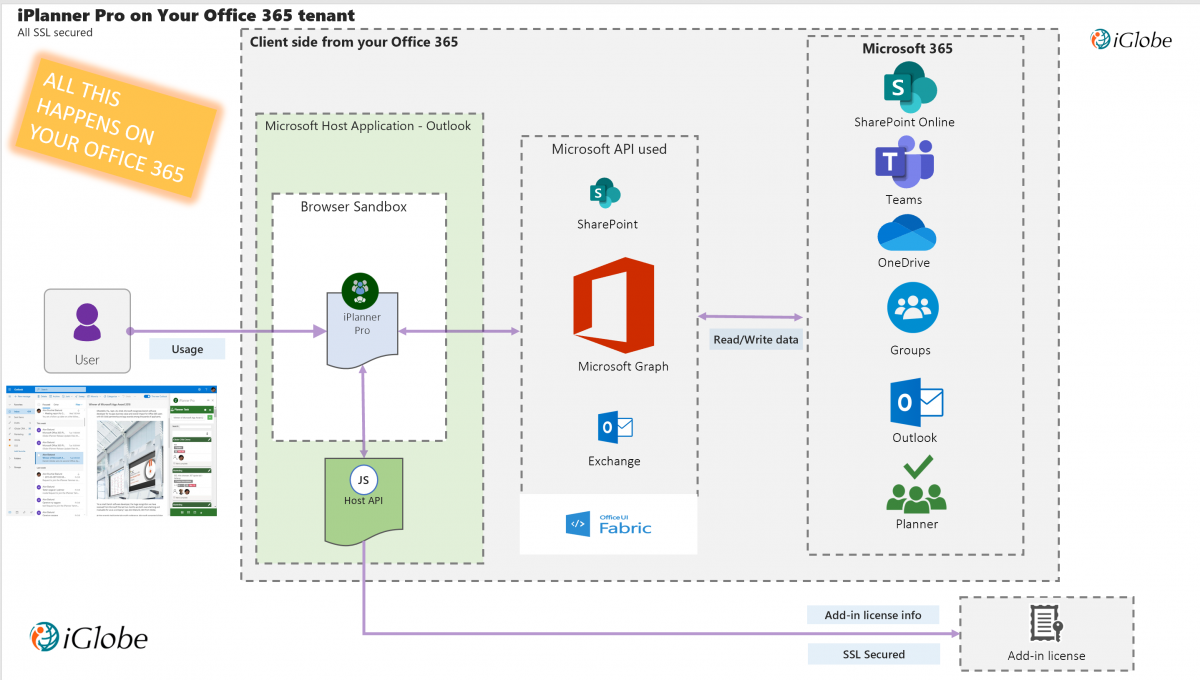
iPlanner Pro is a true Office add-in designed using the Microsoft Office 365 Security model. As all Office Add-ins it contains of a manifest file that defines various settings, including how the add-in integrates with Office clients and to enable IOS and Android availability. The web application and service are hosted iGlobe’s Microsoft Azure. iPlanner Pro is using the Authentication model and make sure the user has a valid token. Using the Microsoft Graph API iPlanner Pro is interacting with several services on Office 365.
iPlanner Pro is an extremely rich Add-in that requires permission using Microsoft Graph to, Planner, Groups, SharePoint, Exchange. Specially Office 365 Groups requires extensive permission. Please notice that the required permissions of Microsoft Graph API are not set by iGlobe but is 100% controlled by Microsoft. If we want to provide you with the functionality your users expect like;
-
-
Display their task information from the Online Planner
-
Create a task from Outlook in the Online Planner
-
Read the e-mail to detect if it contains Attchements
-
Attach a mail to a task (all attachments are saved in the Planner/Group SharePoint Site)
-
Attach a document from the selected mail (all attachments are saved in the Planner/Group SharePoint Site)
-
Save on the Task and into the related SharePoint Group site
-
Copy the subject and body text to the task
-
Save into your and the group calendar
-
Upload a file from local hard drive or from your phone
-
Etc etc
1. Open iPlanner Pro in Outlook click until you get to the last page where you can sign in and give consent as administrator.
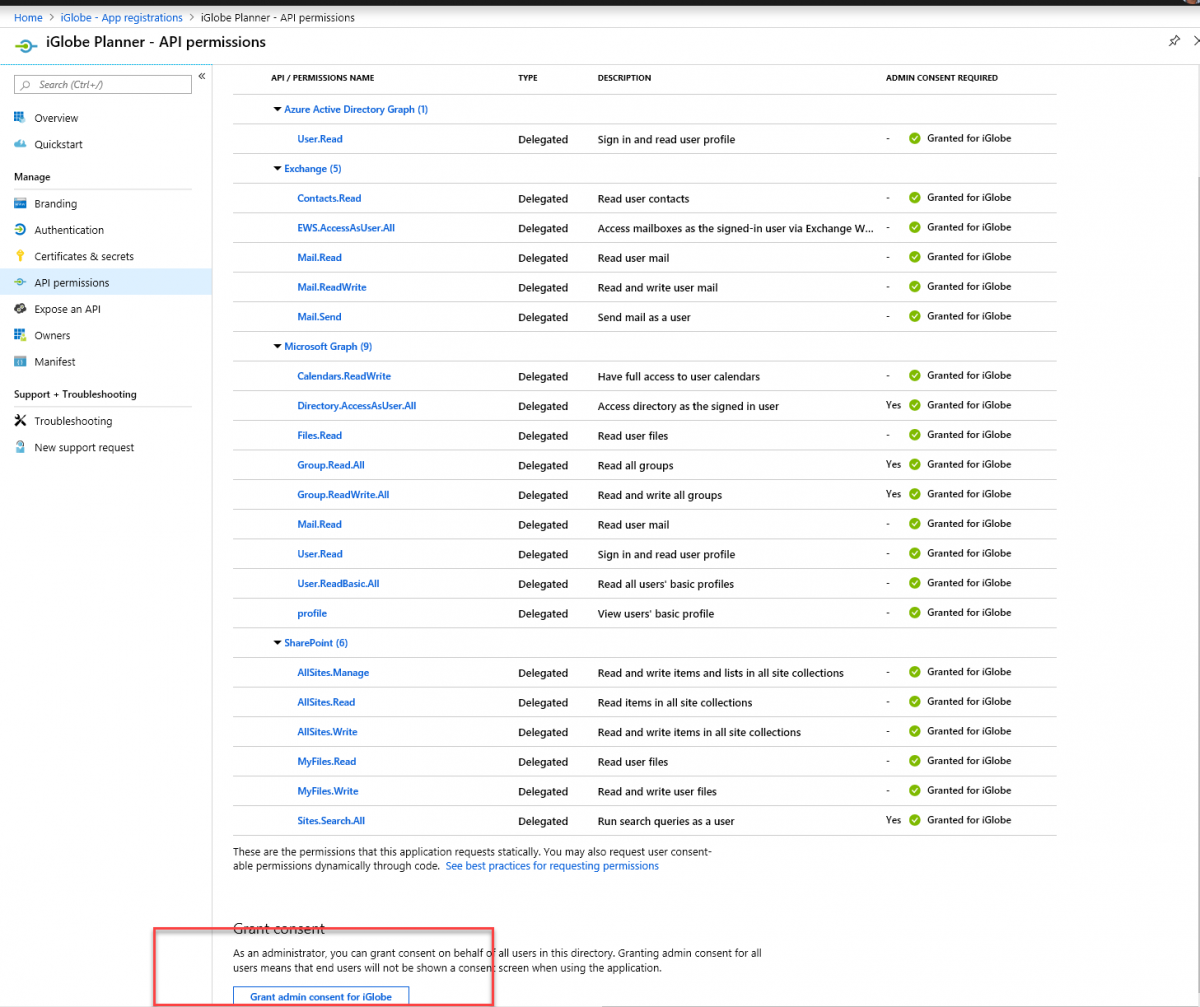
2. Open Azure AD and select app registration - click on iPlanner and select API Permission. At the bottom of the page click on grant admin consent
When you give admin consent from Azure AD.
This means when a Global Administrator authenticate and give permission to iPlanner Pro you can think of this as “let my organization use the iPlanner Pro with the required permission level (see above image) necessary for the iPlanner Pro to provide the functionality the users expect of the Add-in”.
Remember, it is the Add-in that interact with the required Office 365 services! It is not and access you give to people outside your organization or to the Add-in provider.
Second regarding your data.
Data is not saved. We don’t save your data on our server. (we don’t have access or permission). No data are saved locally on any PC. It is an Office add-in that you deploy online. iPlanner Pro will be available on all the user’s devices where the users have a valid Office 365 account with the proper permission given by the Global administrator (the above)
Where’s the data held?
Office 365 splits plan data across a number of repositories. The plan metadata is held in an (your) Azure-based service while the comments for tasks within a plan are stored in the Exchange Online mailbox for the Office 365 Group associated with the plan. Documents and other attachments are held in the SharePoint Online document library belonging to the same Office 365 Group.
This means all data are in your Office 365 environment.
iGlobe (we) host the service. This service is used by all iPlanner Pro customer across the world. But data is on your Office 365. As stated in our EULA we only save information for our license management- Name and e-mail. From the iPlanner User management you can see exactly the same as we can see. This is also, where you have full access to remove and add users.
The GDPR and Security is key issue for us. We relay 100% on Microsoft and are following 100% the requirements they set.
 In short, an Office Add-in extend Office applications and interact with content in Office. Office Add-ins, use familiar web technologies extend and interact with Word, Excel, PowerPoint, OneNote, Project, and Outlook. An Office Add-in can run in Office across multiple platforms, including Office for Windows, Office Online, Office for the Mac, and Office for IOS and Android.
In short, an Office Add-in extend Office applications and interact with content in Office. Office Add-ins, use familiar web technologies extend and interact with Word, Excel, PowerPoint, OneNote, Project, and Outlook. An Office Add-in can run in Office across multiple platforms, including Office for Windows, Office Online, Office for the Mac, and Office for IOS and Android.